EIGRP IPv4 - Authentication
Authentication
EIGRP (Enhanced Interior Gateway Routing Protocol) IPv4 authentication is a security feature that safeguards the integrity and authenticity of routing updates exchanged between EIGRP routers. By implementing authentication, administrators ensure that only trusted routers within the same EIGRP autonomous system can participate in the exchange of routing information. EIGRP supports various authentication methods, with MD5 being a commonly used option. To enable authentication, administrators configure a key chain with a set of cryptographic keys, and routers within the same EIGRP domain are configured with matching keys. The use of MD5 hashes in the authentication process ensures that routing updates exchanged between routers are protected against tampering or unauthorized access. This authentication mechanism adds an essential layer of security to EIGRP, particularly in environments where the confidentiality and reliability of routing information are paramount.
Lab:
Disclaimer
This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to ensure that all material is as complete and accurate as possible, the enclosed material is presented on an Dzas isdz basis. Neither the authors nor Forum assume any liability or responsibility to any person or entity with respect to loss or damages incurred from the information contained in this guide. This configuration guide was developed by Forum. Any similarities between material presented in this configuration guide and any other material is completely coincidental.
Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M), Version 15.2(4)M1, DEVELOPMENT TEST SOFTWARE
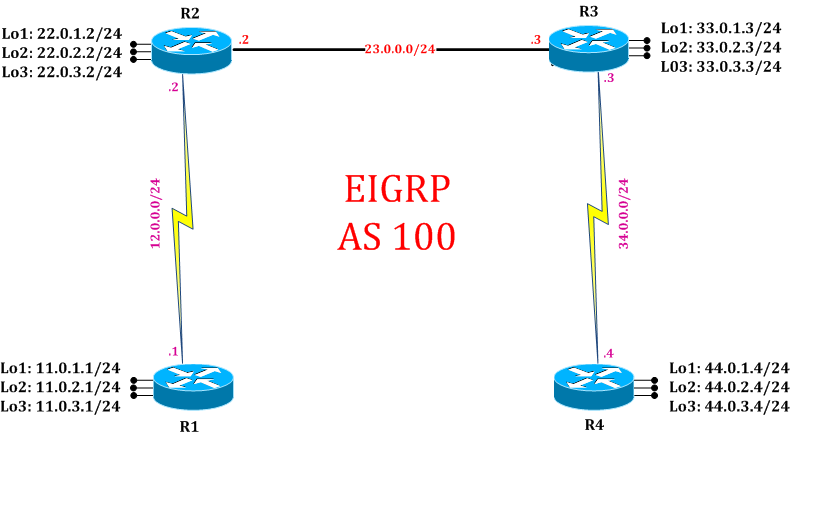
Task 1: Configure IPv4 EIGRP Authentication
Step 1: In the configuration mode of router configure create Key chain and assign key
R1:
key chain akbar (creating a key chain with name akbar)
key 1 (selecting a key 1)
key-string cisco (assigning a key-string by which it will authenticate with, neighbor, which should be same on both the side)
exit
Step 2: Enter the interface where authentication is required and select the encryption mode
R1:
interface serial 2/0
ip authentication mode eigrp 100 md5 (selecting encryption mode MD5)
ip authentication key-chain eigrp 100 akbar (selecting key-chain in which key 1 is selected by which it will authenticate)
exit
Step 3: Enable EIGRP authentication on both the neighbors
R2:
key chain birbal
key 1
key-string cisco
exit
interface serial 2/0
ip authentication mode eigrp 100 md5
ip authentication key-chain eigrp 100 birbal
exit
Task 2: Verification:
Step 1: Verification of authentication by following command:
R1#show running-config (to display the contents of the currently running configuration file or the configuration for a specific class map, interface, map class, policy map, or virtual circuit (VC) class, use the show running-config command in privileged EXEC mode.)
key chain akbar
key 1
key-string cisco
!
interface Serial2/0
ip address 12.0.0.1 255.255.255.0
ip authentication mode eigrp 100 md5
ip authentication key-chain eigrp 100 akbar
!
R2#show running-config
key chain birbal
key 1
key-string cisco
!
!
interface Serial2/0
ip address 12.0.0.2 255.255.255.0
ip authentication mode eigrp 100 md5
ip authentication key-chain eigrp 100 birbal
serial restart-delay 0
!
Step 2: Verify EIGRP neighborship by following command:
R1#clear ip eigrp neighbors
R2#clear ip eigrp neighbors (will flush current OSPF process and initiate fresh OSPF process.)
R1#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 12.0.0.2 Se2/0 14 00:00:17 14 100 0 16
R2#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 23.0.0.3 Et0/0 12 00:00:57 9 100 0 9
0 12.0.0.1 Se2/0 12 00:00:43 17 102 0 13
EIGRP neighbors will authenticate with key and if key matches, EIGRP neighborship will be formed. Fresh EIGRP neighborship can be verified in EIGRP neighbor table.