Network Infrastructure Protection
Network Infrastructure Protection
Network Infrastructure Protection involves the implementation of various measures to safeguard the integrity, confidentiality, and availability of a computer network from potential cyber threats. This comprehensive approach includes deploying advanced security technologies such as firewalls, intrusion detection and prevention systems (IDPS), secure access controls, and encryption protocols. Additionally, regular security audits, vulnerability assessments, and monitoring tools are essential components to identify and respond to potential security risks promptly. Security policies and best practices, coupled with employee training, contribute to creating a security-aware culture within an organization. The overarching goal is to create a resilient and robust network infrastructure that can withstand and mitigate evolving cyber threats, ensuring the continuous and secure operation of critical business processes.
Lab:
For any enterprise, security is a mandatory feature, but when we talk about security, we usually think about perimeter devices like Firewalls, Intrusion Prevention System, Intrusion Detection System, etc. But Security is not just about protecting our perimeter we should protect each point of connection as they may someday or other lead to a point of attack.
One of the ways via which we can controller every point of connection is by deploying Network infrastructure security. Network Infrastructure Protection includes the protection of network devices and their planes. These protection features are almost deployed on every networking and security device in an enterprise.
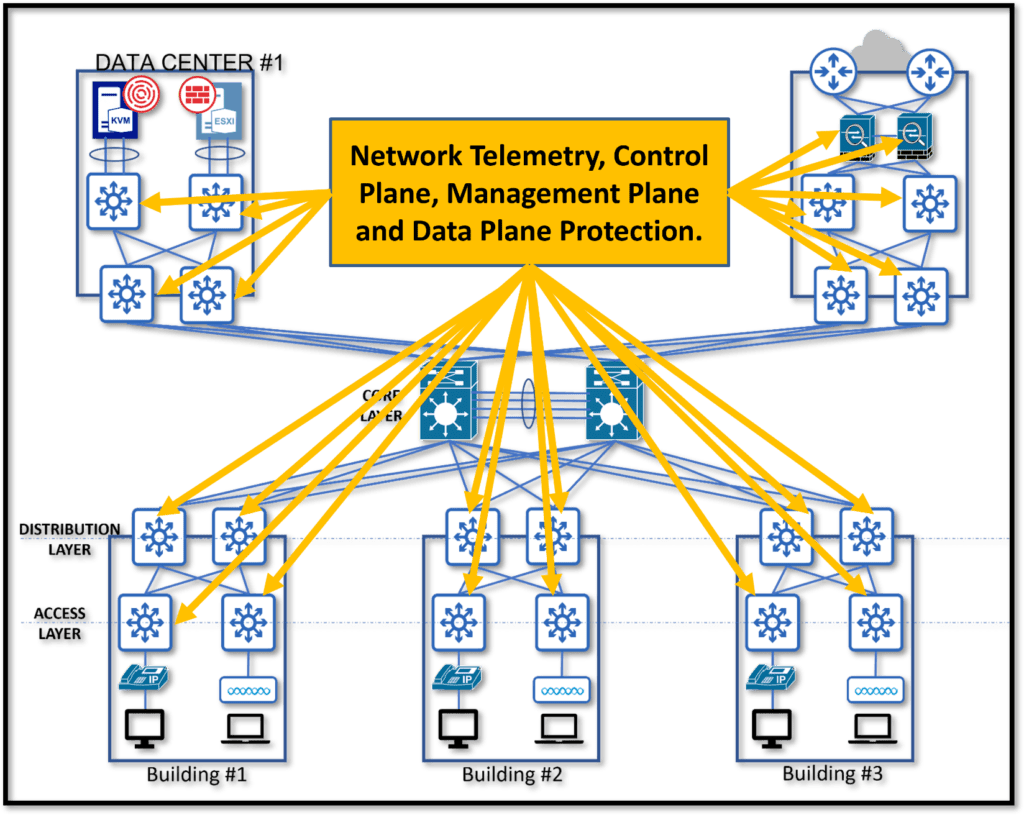
Network Telemetry
Why do we need Network Telemetry?
Let’s say, You, are the lead security architect and the head of Security operations in one of the industry-leading service provider organizations in your country. Your job is to provide security solutions to build and maintain IT infrastructure security in the headquarter campus along with all the branch offices in different countries as well. You are also required to build the Security Incident and Event Management (SIEM) architecture for the network infrastructure to monitor, detect, respond, and deny all kinds of attacks on the IT infrastructure.
To build the Security Operation Center, you and your team have established the following technologies in the infrastructure:
- You installed all kinds of security components in your network, such as an access-list-based gateway router, also known as a zone-based firewall.
- You have also installed the next-generation firewall such as Cisco Firepower with Threat Intelligence and Intrusion Prevention System for perimeter security and protection.
- You have also subscribed for cloud-based perimeter security such as Cisco Umbrella for domain-related security.
- You have configured Layer 2 and Layer 3 security mechanisms to protect routers and switches inside your network.
- You have configured Authentication, Authorization, and Accounting services by integrating technologies like Cisco Identity Services Engine to establish role-based access in your network.
- You have also hardened servers and established endpoint protections such as Anti-virus, Anti-spyware, Anti-ransomware, Data loss protection, and encryption on all your edge devices.
But we already know that each entry point in your network can be a source of an attack. Since the attack surfaces are ever-growing and new vulnerabilities are found in existing systems every other day, it is still possible for an adversary to penetrate your network and take illegal access of your systems using various techniques. For example, an attacker may first scan your public IP addresses for open services and/or hijack sessions using different techniques, if successful, the attacker may try to bypass the firewall by creating custom packets that match your access lists. Then, attacker may try to reroute traffic from your network and perform a man-in-the-middle attack or scan your internal network for the number of live devices such as servers. Attackers try to assess the vulnerabilities in the servers which they may exploit to gain access to the system and perform data exfiltration or deploy ransomware scripts. In such cases, just deploying and configuring security components is not enough. The defense needs something to detect threats and events like these in real-time to identify malicious traffic and gather as much information possible to stop the attack and trace the adversary for legal actions.
As a security architect at one of the industry-leading organizations, you must detect and break the chain of events that point towards an attack on your organization before the attack is successful. To achieve this, you will need a real-time data monitoring of each element in your network to find the elements of the attack including, and to also known the exact time when the attack was launched, and to know the source of the attack, the destination of the attack, and the type of attack, the vulnerability that was being exploited, the type of malware that was being used, logs generated on the system, etc.
But how will you gather so much data and in an organized, readable structure? This is where Network Telemetry comes in.
What is Network Telemetry?
Network telemetry is gaining information about the network, collection of all the data about the network including but not limited to communications, protocols used, devices used, device information, time information, and processing information. All this information is collected on a centralized management server to monitor and analyze the whole network infrastructure so that as soon as a problem arises, an alert can be generated, and engineers can fix the issues before a damaging impact occurs.
To collect so much information, network telemetry uses the following protocols and information to generate organized informational real-time data for analysis and monitoring:
-
NTP:
Network Time Protocol is a protocol used for time synchronization between different systems. Time synchronization becomes a necessity in Network Telemetry because if there is an outage or downtime at one place and the centralized management system is at another location, the alerts with different time stamps may create several problems in fixing problems. There can be a time difference of several hours, especially in MNCs with multiple branch offices. For example, in MNCs, there are ticketing systems used for generating system issue requests that need to be fixed. If one ticket is generated in America and the technical engineer is in India, there is a time difference of about 12hours approximately, because of which the timestamp on the ticket shows a ticket generated that is 12 hours ago and the engineer might lose track of the issue. NTP solves this problem by synchronizing the time between the systems in America and India so the alerts that have been generated are tracked seamlessly. Also, if your network is being compromised from overseas, the time the attack was launched and the time you see the alert generated may be different due to different time zones. This is where NTP protocol helps to synchronize the time differences to help understand the incident better. -
Syslog:
Every device has sensors in each of its hardware components. These sensors collect data of the respective hardware components and send it to the device software which in turn generates and stores the log messages of the device. These log messages in networking devices are called Syslog messages. These Syslog messages are sent to the centralized management platform for analysis and to monitor, detect and perform root cause analysis of all the problems with the network devices. -
NetFlow:
NetFlow is a network protocol that was developed by Cisco, for collecting all IP traffic information and for monitoring network flow. By Analyzing NetFlow data, you can get a bigger picture of network traffic flow and the volume of the data that is being transmitted over the network. By monitoring and analyzing the data provided by NetFlow, a security administrator can determine things such as the source and destination of traffic, type of service, and the causes of the attack. A general traffic flow monitoring and analysis using NetFlow consist of three main things: -
Flow exporter: Combines packets into flows and sends flow records towards one or more flow collectors.
-
Flow collector: responsible for receiving, storing, and pre-processing of traffic flow data received from a flow exporter.
-
Analysis application: analyzes received traffic flow data in the terms of incoming attacks or creates a profile of the normal traffic by using network traffic statistics.
Using these three main components: NTP, Syslog, and NetFlow, all the traffic and devices used in the organization’s network can be monitored and threats and problems can be detected in real-time, and incidents can be handled before any serious damage occurs to the organization.